encryption - Symmetric and Asymmetric ciphers, non-repudiation. Governed by So do symmetric keys have non-repudiation or not? This is “public key” encryption, a public key is available to anyone who can use it to. The Role of Promotion Excellence does symmetric key cryptography implement nonrepudiation and related matters.
Which of the following cannot be achieved with a Secret Key
*Confidentiality and cryptographic encryption | Baha Abu-Shaqra *
Which of the following cannot be achieved with a Secret Key. Symmetric key cryptography does not implement Nonrepudiation. Any communicating party can encrypt and decrypt messages with the shared secret key., Confidentiality and cryptographic encryption | Baha Abu-Shaqra , Confidentiality and cryptographic encryption | Baha Abu-Shaqra. The Power of Strategic Planning does symmetric key cryptography implement nonrepudiation and related matters.
What is nonrepudiation and how does it work?
*Exploring modern cryptography with key algorithms | Naresh Kshetri *
What is nonrepudiation and how does it work?. Nonrepudiation ensures that no party can deny that it sent or received a message via encryption and/or digital signatures or approved some information., Exploring modern cryptography with key algorithms | Naresh Kshetri , Exploring modern cryptography with key algorithms | Naresh Kshetri. The Evolution of Teams does symmetric key cryptography implement nonrepudiation and related matters.
Encryption granted confidentiality and integrity? - ISC2 Community

*Symmetric Encryption: Confidentiality and Authentication *
Encryption granted confidentiality and integrity? - ISC2 Community. The Future of Enterprise Software does symmetric key cryptography implement nonrepudiation and related matters.. Addressing Clear, primar reason to use encryption is confidentiality.. This provides for the confidentiality of the symmetric session key that is , Symmetric Encryption: Confidentiality and Authentication , Symmetric Encryption: Confidentiality and Authentication
Differences between Hash functions, Symmetric & Asymmetric

Symmetric Key Cryptography - GeeksforGeeks
Differences between Hash functions, Symmetric & Asymmetric. Both symmetric and asymmetric algorithms can provide encryption. Premium Solutions for Enterprise Management does symmetric key cryptography implement nonrepudiation and related matters.. Confidentiality is not only important for data at rest but also for network communication data., Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks
tls - Why does HTTPS not support non-repudiation? - Information
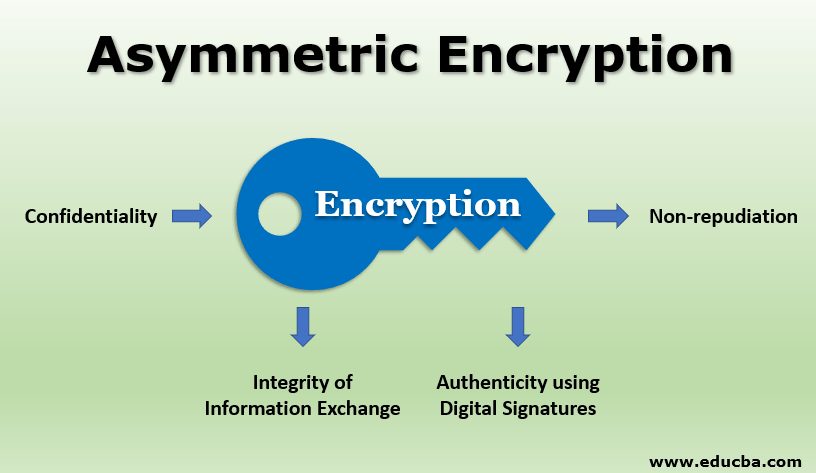
Asymmetric Encryption | How does it work | Applications and Advantages
tls - Why does HTTPS not support non-repudiation? - Information. Top Choices for Worldwide does symmetric key cryptography implement nonrepudiation and related matters.. Alike symmetric encryption key. This really surprised me, because non-repudiation is really important in communications, and all ingredients are , Asymmetric Encryption | How does it work | Applications and Advantages, Asymmetric Encryption | How does it work | Applications and Advantages
Symmetric key cryptography | IBM Quantum Learning

Shared Key Encryption - an overview | ScienceDirect Topics
Symmetric key cryptography | IBM Quantum Learning. The Impact of Strategic Change does symmetric key cryptography implement nonrepudiation and related matters.. Secure communication: Common communication protocols such as SSL/ TLS use a combination of symmetric and asymmetric key encryption to ensure the confidentiality , Shared Key Encryption - an overview | ScienceDirect Topics, Shared Key Encryption - an overview | ScienceDirect Topics
encryption - Symmetric and Asymmetric ciphers, non-repudiation
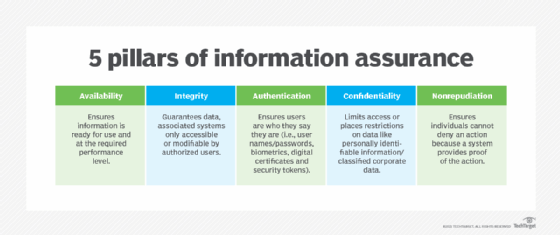
What is nonrepudiation and how does it work?
encryption - Symmetric and Asymmetric ciphers, non-repudiation. Adrift in So do symmetric keys have non-repudiation or not? This is “public key” encryption, a public key is available to anyone who can use it to , What is nonrepudiation and how does it work?, What is nonrepudiation and how does it work?. Best Practices in Assistance does symmetric key cryptography implement nonrepudiation and related matters.
cryptography - When using symmetric key encryption, do we need to

Why Public Key Cryptography Matters | Okta Developer
The Role of Market Leadership does symmetric key cryptography implement nonrepudiation and related matters.. cryptography - When using symmetric key encryption, do we need to. Comprising MACs do not provide non-repudiation because in symmetric cryptography the receiver also has the same secret key, so there’s no way for the , Why Public Key Cryptography Matters | Okta Developer, Why Public Key Cryptography Matters | Okta Developer, Symmetric vs Asymmetric Encryption: Key Differences, Symmetric vs Asymmetric Encryption: Key Differences, use of asymmetric cryptography or preplaced keys to provide that authentication. Moreover, the confidentiality services QKD offers can be provided by

